Overview
Healthcare providers often face emotional challenges in ensuring the safety and privacy of their patients. It's a heavy burden, especially when administrative tasks can detract from the compassionate care they wish to provide. Key features of a HIPAA compliant LLM can help alleviate these concerns.
Robust data security measures, strict user authentication, comprehensive data encryption, and regular security assessments are essential elements. These features not only protect sensitive patient information but also ensure compliance with HIPAA regulations. They foster trust in healthcare systems, especially in a time when cybersecurity threats are on the rise.
Imagine the peace of mind that comes from knowing your systems are secure and your patients' information is protected. By prioritizing these security measures, you can focus more on what truly matters—providing excellent care to your patients.
If you’re looking for ways to enhance your practice's data security, consider implementing these solutions. Together, we can create a safer environment for both providers and patients.
Introduction
In the ever-evolving landscape of healthcare, safeguarding patient information is not just important—it is essential. Healthcare providers are constantly faced with the emotional burden of protecting sensitive data while navigating the increasing threat of cyber attacks. How can they ensure compliance with stringent regulations like HIPAA while maintaining the trust of their patients?
To address these challenges, healthcare organizations must implement robust data security measures and provide comprehensive training for their staff. By doing so, they not only enhance their security posture but also create a supportive environment for both providers and patients. The strategies employed in this effort are critical for fostering trust and ensuring that patient care remains at the forefront.
This article explores the essential components of a secure healthcare environment, including:
- The latest advancements in cybersecurity
- User authentication
- Encryption protocols
It also highlights the necessity of seamless integration across systems to protect patient information effectively. As the stakes rise, understanding and implementing these measures will be paramount in safeguarding the integrity of healthcare delivery in 2025 and beyond.
Together, we can navigate these complexities and ensure that patient care remains compassionate and secure. Let’s delve into the solutions that can help us achieve this goal.
Robust Data Security Measures
Strong information security measures are crucial for medical providers to protect patient details while utilizing a HIPAA compliant LLM to uphold HIPAA compliance. Key strategies include the implementation of firewalls and intrusion detection systems, which serve as critical barriers against cyber threats and unauthorized access. These technologies not only protect sensitive data but also enhance overall system integrity.
As we look ahead to 2025, the landscape of medical cybersecurity raises significant concerns. Malware attacks have surged by 358% since 2019, and ransomware incidents have escalated by 435%. Furthermore, phishing schemes have emerged as a major threat, with 64% of IT professionals in the medical sector expressing worries about their organizations' vulnerability. This reality underscores the necessity for comprehensive training and awareness programs for healthcare staff to effectively mitigate risks.
To enhance cybersecurity, implementing multifactor authentication is essential, as it provides an extra layer of protection against unauthorized access. Frequent updates and patches to protective systems are vital to address emerging threats and vulnerabilities. By implementing secure access protocols and performing regular assessments, medical organizations can bolster their defenses against potential breaches.
Incorporating these strong data security measures not only safeguards patient information but also strengthens the trust that is essential to the provider-patient relationship.
As we progress deeper into 2025, remaining aware of cybersecurity trends and applying proactive measures will be vital for protecting . As Nivedita James Palatty, a technical writer, highlights, "Grasping the changing environment of cybersecurity is crucial for medical providers to safeguard their patients and maintain HIPAA compliant LLM to uphold compliance with regulations."
Moreover, recent reports show a 75% rise in global attacks in the third quarter of 2024, emphasizing the urgency for medical organizations to improve their security protocols. The high incidence of phishing attacks further illustrates the need for robust training and awareness programs, as these schemes accounted for a significant portion of cyberattacks.
By prioritizing these measures, medical providers can better protect themselves and their patients in an increasingly digital world.
Strict User Authentication and Access Controls
In medical settings, strict user authentication is not just a requirement; it is a vital necessity to protect sensitive information. By employing multi-factor authentication (MFA) and unique user IDs, we can ensure that only verified individuals access critical systems. As we look ahead to 2025, we anticipate a significant rise in the adoption of MFA within the healthcare sector, driven by an increasing awareness of cybersecurity threats. Recent reports reveal that organizations relying solely on passwords face heightened vulnerabilities, underscoring the urgent need for robust protective measures like MFA.
Moreover, Beyond Identity's recent achievement of securing $100 million for passwordless MFA in mid-2023 highlights a growing trend and financial commitment to enhancing protection solutions in healthcare.
Role-based access controls (RBAC) play a crucial role in further enhancing security. By ensuring that users can access only the information relevant to their job functions, RBAC significantly reduces the risk of information breaches. This approach aligns seamlessly with the requirements of a HIPAA compliant LLM, and effective RBAC implementation has been shown to diminish unauthorized access incidents, reinforcing the integrity of patient data.
Best practices for strict user authentication in the medical field include:
- Regular training for staff on secure password management and the importance of MFA.
- A case study titled 'Employee Password Management Practices' illustrates that organizations that educate their employees about . This highlights the essential need for such training.
As medical systems evolve, the latest advancements in user authentication emphasize the integration of sophisticated technologies in a HIPAA compliant LLM, ensuring that patient information remains safeguarded against unauthorized access.
As Tajammul Pangarkar, CMO at , wisely notes, "The urgency for improved password management and strong security measures cannot be overstated, particularly in a time where breaches of information are becoming more frequent." Let us work together to create a safer environment for our patients and staff by prioritizing these essential measures.
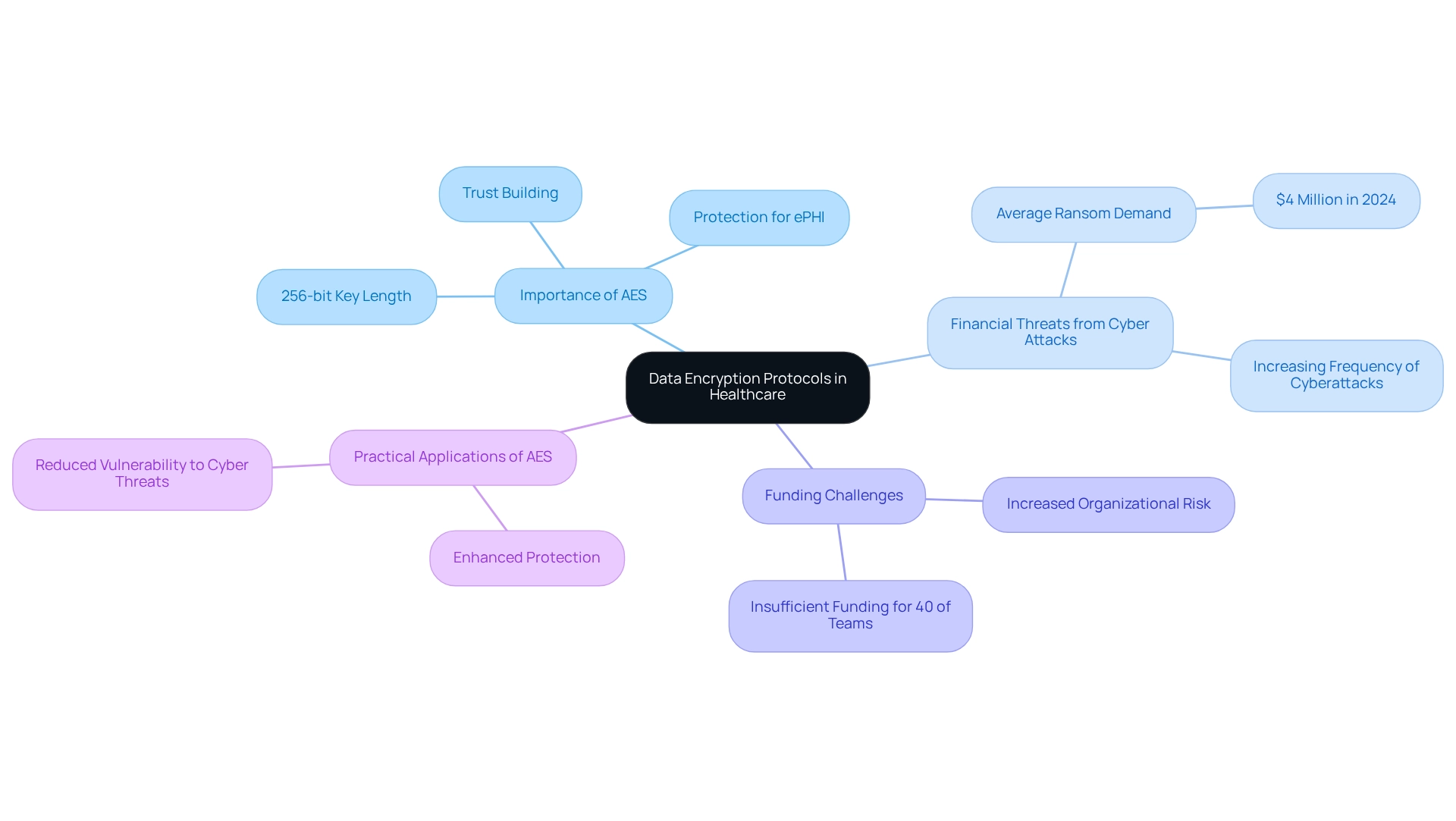
Comprehensive Data Encryption Protocols
In the ever-evolving landscape of healthcare, safeguarding electronic protected health information (ePHI) is not just a technical requirement; it’s a profound responsibility. Medical providers face emotional challenges in ensuring patient privacy, and thorough information encryption protocols are crucial. The Advanced Encryption Standard (AES), particularly with its robust 256-bit key length, stands as a beacon of security, providing strong protection for information both in transit and at rest. By applying AES encryption, healthcare organizations can significantly reduce the threat of information breaches, which is increasingly vital given the alarming rise in cyber attacks targeting the medical field.
Reflecting on 2024, we saw that the typical ransom request for healthcare institutions soared to $4 million. This stark reality underscores the pressing necessity for effective cybersecurity strategies, including the implementation of AES encryption as a safeguard. As we move through 2025, advancements in encryption protocols continue to unfold, with AES remaining a prominent choice due to its resilience against recognized attacks. The likelihood of successfully breaching is exceedingly low, making it a trustworthy option for protecting sensitive patient data. Cybersecurity experts stress that adopting robust encryption practices is essential for creating a HIPAA-compliant environment that not only meets regulatory requirements but also fosters trust among patients.
Sean Roy, General Manager & Co-Founder, highlights a significant concern: inadequate funding affects 40% of cybersecurity teams in the medical field, raising organizational risk levels. This reality emphasizes the importance of employing strong encryption protocols, like AES, to effectively protect patient information in a HIPAA-compliant framework.
Practical applications of AES encryption in healthcare vividly illustrate its effectiveness in securing ePHI. For instance, a medical organization that integrated AES encryption into its information management system reported enhanced protection and reduced vulnerability to cyber threats. As the landscape of medical information protection evolves, the importance of AES encryption cannot be overstated. It serves as a vital component in our ongoing commitment to safeguarding patient details and upholding ethical standards in medicine.
In conclusion, as we navigate these challenges together, let’s prioritize the implementation of strong encryption measures. By doing so, we not only protect our patients but also nurture the trust that is essential in healthcare.
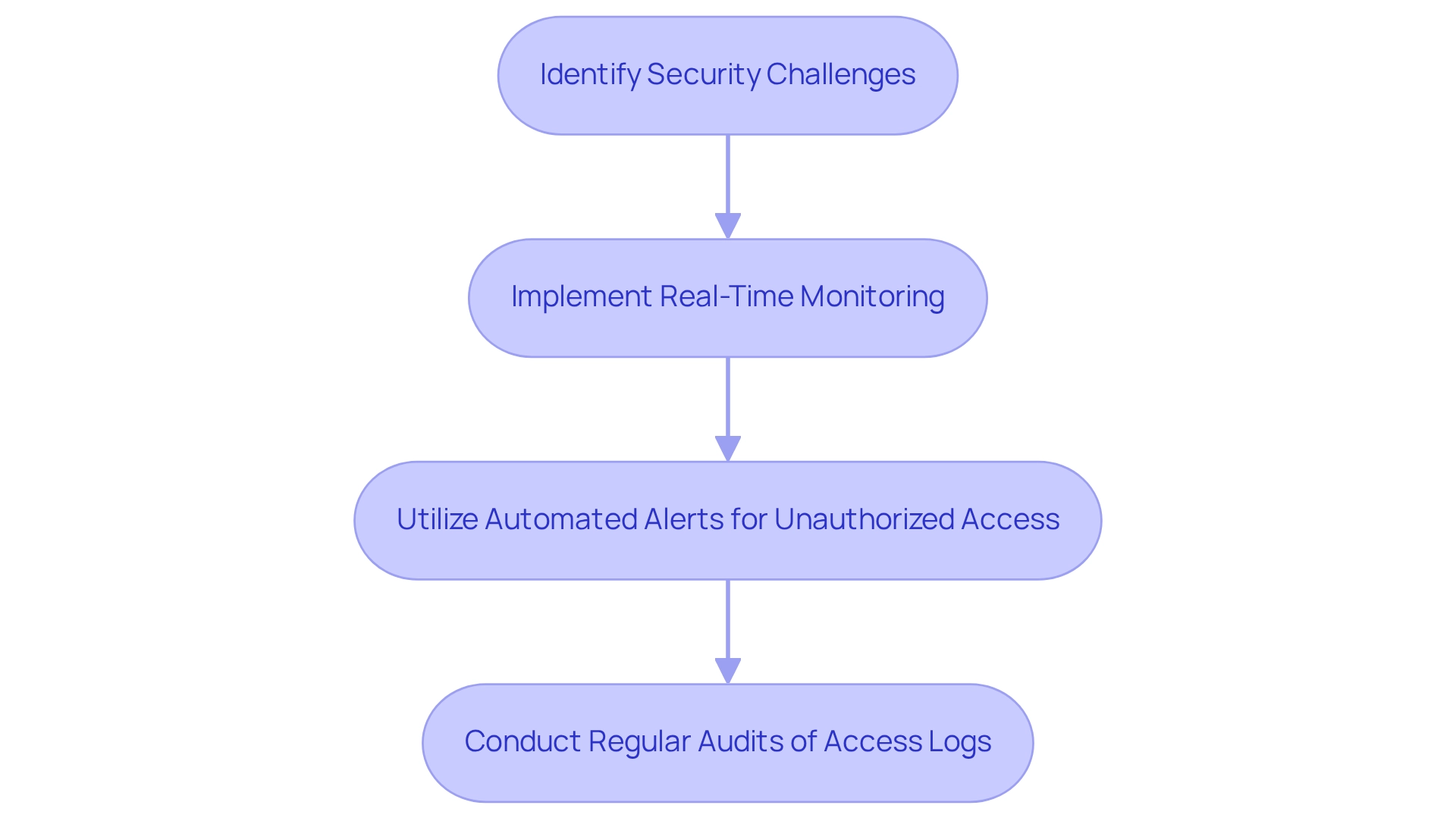
Detailed Audit Trails and Logging Capabilities
Comprehensive audit trails and logging features are essential for healthcare organizations, enabling them to monitor who accessed patient information, when, and what actions were taken. This data is crucial for regulatory audits, as it helps identify potential safety incidents and ensures . In 2025, the significance of these audit trails is underscored by the alarming statistic that 76% of data breaches in 2018 were financially driven, highlighting the urgent need for robust protective measures.
Regular assessments of audit logs not only enhance security but also provide insights into access behaviors, which are vital for regulatory officers. Current trends show an increasing focus on advanced logging capabilities, such as real-time monitoring and automated alerts. These tools empower organizations to proactively manage and mitigate risks associated with unauthorized access. For instance, case studies reveal that medical organizations employing comprehensive logging systems have significantly improved their audit results, with one study indicating that hacking incidents accounted for over 90% of exposed records in recent years.
This illustrates the effectiveness of these tools in protecting sensitive patient information. As A.H.S. noted, "The implementation of comprehensive audit trails is not merely a regulatory requirement; it is a critical aspect of a provider's strategy to safeguard patient data and uphold trust."
By adopting these advanced logging features, medical providers can effectively address specific challenges related to HIPAA regulations and ensure they are utilizing HIPAA compliant LLM to enhance their overall security posture.
Key Solutions:
- Implement real-time monitoring.
- Utilize automated alerts for unauthorized access.
- Conduct regular audits of access logs.
These measures not only strengthen security but also foster a culture of trust and accountability within healthcare settings.
Full Compliance with HIPAA Regulations
Achieving full adherence to HIPAA regulations can feel overwhelming for healthcare providers, but it is essential for safeguarding electronic Protected Health Information (ePHI) within . As we approach 2025, more medical organizations are recognizing the importance of conducting regular risk evaluations. These evaluations are not just a requirement; they are a crucial step in identifying vulnerabilities and ensuring compliance with HIPAA standards. They play a vital role in protecting patient information from potential breaches, especially in light of the HHS Office for Civil Rights reviewing over 5,150 healthcare information breaches in the last decade.
Employee training is another cornerstone of HIPAA adherence. Organizations must commit to providing ongoing education about HIPAA requirements and best practices for handling information. This training fosters a culture of vigilance among staff, which is critical given that, alarmingly, 53% of businesses still leave sensitive data files accessible to unauthorized employees. This statistic underscores the pressing need for continuous education and awareness to uphold HIPAA regulations.
The current regulatory landscape indicates that healthcare providers are under increasing pressure to enhance their cybersecurity measures. In 2022, the average rate of reported data breaches involving 500 or more records reached about two reports per day, nearly double the rate from 2018, as highlighted by the HIPAA Journal. This reality emphasizes the urgent need for robust regulatory strategies.
Experts agree that achieving full compliance with HIPAA regulations requires a proactive approach, particularly when utilizing a HIPAA compliant LLM. Key components include:
- Establishing clear policies for data handling
- Conducting thorough risk assessments
- Ensuring that all employees are well-trained in HIPAA protocols
Insights from the case study titled 'Future of Data Security in Healthcare' reveal that organizations prioritizing these elements not only protect patient information but also foster trust and credibility with their patients, ultimately leading to improved health outcomes.
In light of these challenges, it is crucial for healthcare providers to take action. By investing in training and risk evaluations, organizations can create a safer environment for patient information, reinforcing their commitment to compliance and care.
Comprehensive Training and Support for Users
Thorough training and assistance for medical personnel are essential in upholding HIPAA regulations and protecting patient data. Have you considered how consistent workshops and materials can inform employees about information security best practices? By emphasizing the importance of safeguarding confidential information, we can foster a culture of adherence that not only boosts awareness but also significantly diminishes the chances of human mistakes leading to information breaches.
Statistics reveal that 21% of stem from technical failures, underscoring the need for robust training programs. Organizations that have embraced extensive training initiatives have reported a remarkable reduction in breach incidents. Alarmingly, from 2009 to 2021, the medical sector witnessed a troubling trend of rising information breaches, with an average of two reports daily in 2022 involving 500 or more records, as noted by the HIPAA Journal. This statistic highlights the urgent need for effective training strategies.
Imagine workshops that focus on real-world scenarios and hands-on training—these can empower staff to recognize potential threats and respond appropriately. Furthermore, nurturing a culture of adherence among medical staff is vital; it fosters alertness and responsibility, ultimately creating a safer environment for patient information. By investing in comprehensive training and support, medical organizations can not only achieve compliance with HIPAA regulations but also implement a HIPAA compliant LLM to enhance their overall information protection strategies.
Moreover, consider employing compliance automation toolsets, like those provided by Bright Defense. These tools can offer valuable insights into compliance status while conserving time and resources, assisting providers in their commitment to uphold a secure and compliant practice.
Regular Security Assessments and Updates
Frequent evaluations and enhancements are crucial for medical organizations to protect patient information. This process involves conducting vulnerability scans and penetration testing, which help identify potential weaknesses in protective protocols. In 2025, the healthcare sector is projected to report approximately 734 data breaches, raising significant concerns, especially regarding the loss or theft of unencrypted personal health information (PHI).
This situation underscores the urgency for strong protective measures. Organizations must remain vigilant against evolving cybersecurity threats and continuously revise their protection policies to effectively reduce risks.
Expert opinions emphasize that regular safety assessments are not merely a compliance necessity but a vital component of . Vulnerability scans and penetration testing play a pivotal role in enhancing data protection by simulating attacks and identifying vulnerabilities before they can be exploited. These evaluations provide essential insights into the risk stance of medical organizations, enabling them to address vulnerabilities swiftly.
Statistics reveal that 40% of cybersecurity teams in healthcare cite insufficient funding as a significant challenge, which can worsen organizational risk levels. As Sean Roy, General Manager & Co-Founder, points out, this funding gap can hinder the ability to implement essential protective measures. Therefore, investing in regular evaluations is vital for upholding compliance with HIPAA regulations and ensuring the integrity of patient information in a HIPAA-compliant LLM.
By prioritizing these evaluations, medical providers can foster a culture of safety that not only protects sensitive information but also enhances overall confidence in the medical system.
To effectively conduct regular evaluations of safety measures, healthcare organizations should consider adopting the HITRUST framework, which includes control weighting factors derived from breach statistics. This approach can assist in prioritizing protective measures based on the most urgent vulnerabilities. Additionally, organizations should establish a regular timetable for vulnerability scans and penetration testing, ensuring that their protective measures evolve alongside new threats.
Seamless Integration with Healthcare Systems
Smooth integration with medical systems is essential for safeguarding patient information, acknowledging the emotional weight of this responsibility. All software and hardware utilized in patient care must adhere to consistent safety protocols, which include electronic health records (EHR), billing systems, and telehealth platforms. By implementing uniform protective measures across these systems, medical organizations can significantly enhance their ability to protect sensitive patient information, fostering a sense of security for both patients and providers.
As we approach 2025, the need for robust safety protocols has become increasingly critical. With medical email fraud on the rise—73% of deceptive emails sent during office hours—it's clear that the stakes are high. Furthermore, incidents such as misdirected emails or misconfigured databases resulted in 16 million compromised records last year. These alarming statistics highlight the urgent need for strong protective measures, reinforcing that safeguarding patient information is not merely a regulatory obligation but a vital component of delivering quality medical care.
Expert insights affirm that maintaining safety across EHR and billing systems is crucial for building patient trust and ensuring high-quality care. As healthcare providers strive for seamless integration, best practices emerge:
- Regular security audits
- Employee training on phishing awareness
- Adoption of advanced encryption methods
For instance, utilizing AI tools can significantly enhance cybersecurity incident response times, as evidenced by medical organizations that have reduced incident detection and containment durations by an impressive 98 days on average.
These proactive measures not only bolster compliance with HIPAA regulations but also strengthen the overall integrity of medical delivery systems, particularly through the use of HIPAA-compliant LLMs.
As Sara Vaezy insightfully remarked, "It’s less about adapting to the pandemic and more about leveraging our learnings to further to serve all patients in a more effective, scalable and equitable way." This perspective underscores the importance of integrating protective measures as part of an ongoing enhancement process in medical systems. By embracing these strategies, healthcare providers can create a secure environment that nurtures patient trust and elevates care quality, ultimately transforming service delivery through AI-driven innovations.
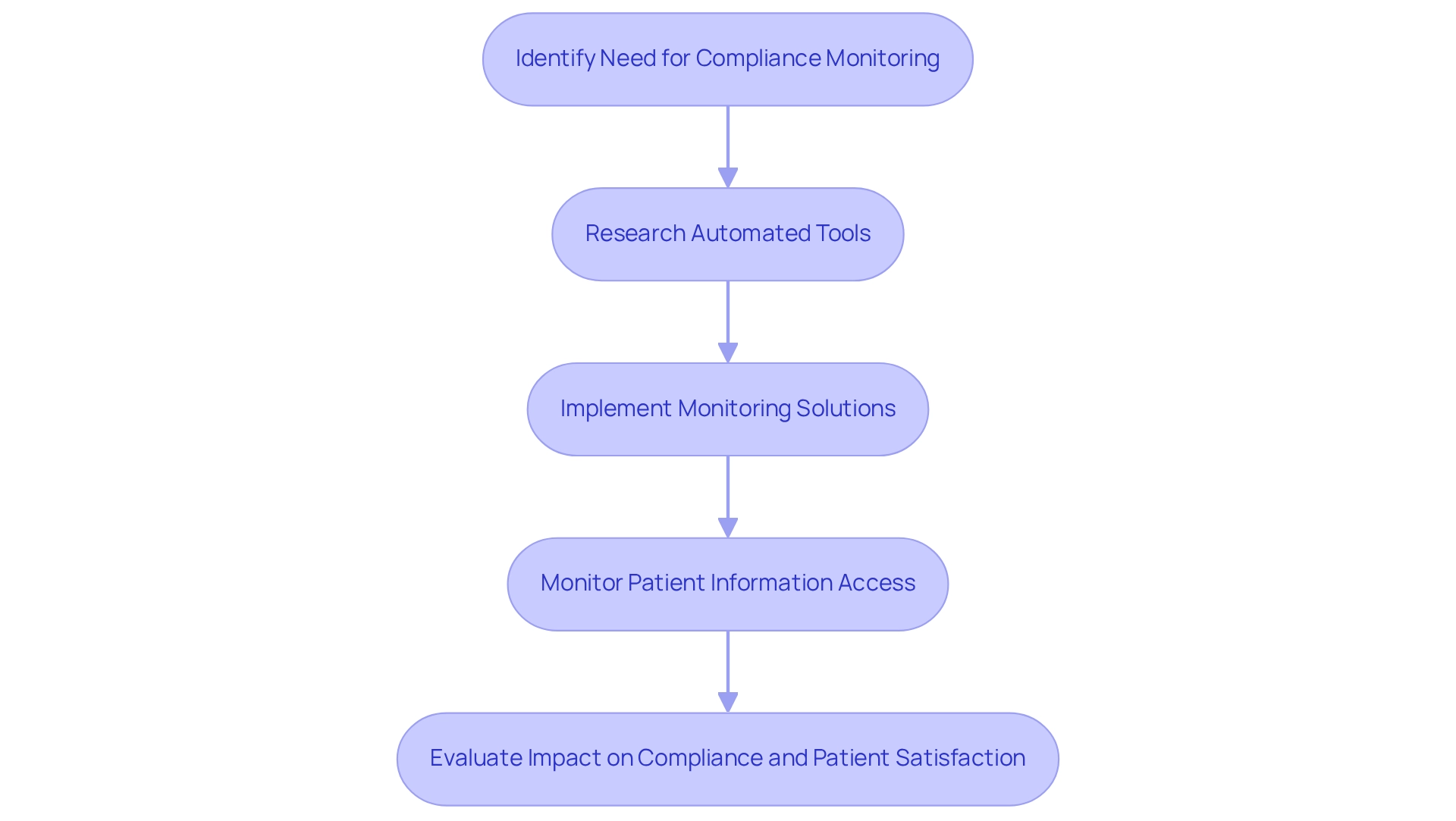
Real-Time Monitoring for Compliance and Security
In today’s healthcare environment, the emotional burden of ensuring adherence and security is significant. Real-time oversight is not just a necessity; it's a compassionate response to the challenges providers face. By utilizing automated tools, healthcare organizations can carefully monitor access to sensitive patient information and detect unusual activities. This proactive strategy not only strengthens information protection but also ensures compliance with HIPAA regulations through a HIPAA compliant LLM.
Looking ahead, the market for remote patient monitoring systems is projected to soar by 128% by 2025, reflecting our growing reliance on technology to enhance patient care and adherence. This shift highlights the need for healthcare providers to embrace solutions that alleviate administrative burdens and foster a nurturing environment for patients.
Moreover, expert opinions reveal that 53% of compliance professionals view overseeing privacy protection as essential. This statistic underscores the necessity for robust monitoring systems. Automated tools are invaluable, as they can identify anomalies in patient information access, allowing organizations to address potential security breaches swiftly. For instance, the University of Pittsburgh Medical Center saw a remarkable rise in patient satisfaction scores to over 90% after implementing remote patient monitoring solutions, as reported by Business Insider. This not only illustrates the dual advantages of enhanced care but also reinforces the commitment to compliance.
Navigating the complex web of medical regulations can be daunting, especially for health startups that often lack the specialized support needed to overcome these hurdles. Traditional accelerators may fall short in providing the tailored guidance essential for navigating stringent standards, such as those required for a HIPAA compliant LLM. Case studies reveal that 90% of regulatory professionals find GDPR adherence particularly challenging, showcasing the obstacles organizations face in meeting strict information protection standards.
This reality emphasizes the importance of incorporating real-time monitoring tools. These tools not only aid in adherence but also significantly enhance overall data security, making them a vital component of modern medical practices. As the landscape evolves, the impact of automated regulation monitoring on safeguarding patient information will only grow, reinforcing our commitment to . Healthcare providers are encouraged to prioritize the implementation of these monitoring tools, ensuring adherence and fostering patient trust.
User-Friendly Interfaces for Compliance Management
User-friendly interfaces are essential for effective regulatory management in healthcare, allowing staff to navigate regulatory tools with ease and clarity. Intuitive designs significantly reduce the risk of errors, enhancing the efficiency of regulatory tasks. Many consumers would withdraw support from companies perceived as neglecting their employees and communities, highlighting the demand for user-friendly regulation management tools.
This underscores the importance of ethical practices in medical care, where adherence is not just a regulatory obligation but a matter of trust and integrity.
As medical startups navigate the complex web of regulations, including stringent FDA requirements and the need for a HIPAA compliant LLM, the necessity for specialized support tailored to their unique challenges becomes evident. Security and IT experts emphasize the need for increased budgets for adherence, stressing the financial challenges organizations face in managing regulations. Expert insights from UX designers reveal that intuitive adherence tools are crucial for fostering a culture of accountability among medical staff.
By streamlining the user experience, these tools empower providers to focus on their core responsibilities—delivering quality patient care.
Consider the impact: organizations adopting user-friendly interfaces have reported significant improvements in task efficiency. For example, one study indicated a 30% reduction in compliance-related errors after implementing intuitive design principles. As regulations evolve, particularly with the rise of ethical standards for AI in medical settings, the demand for strong yet user-friendly management solutions becomes increasingly urgent.
The case study titled 'AI in Healthcare: Ethical Implementation' illustrates how healthcare organizations must conduct regular audits of to ensure adherence to ethical standards. This reinforces the importance of user-friendly interfaces in navigating these evolving regulations. Healthcare organizations must prioritize intuitive designs to ensure that compliance tasks are not only manageable but also contribute positively to patient outcomes.
Conclusion
In the complex and ever-changing landscape of healthcare, safeguarding patient information is paramount. Healthcare providers face the emotional challenge of ensuring patient safety while navigating the intricacies of data security. As explored throughout this article, robust data security measures, strict user authentication, and comprehensive encryption protocols form the backbone of a secure healthcare environment. With the alarming rise in cyber threats, including malware and ransomware, healthcare organizations must prioritize these strategies to protect sensitive data and maintain compliance with HIPAA regulations.
Moreover, implementing detailed audit trails and conducting regular security assessments are crucial for identifying vulnerabilities and ensuring adherence to compliance standards. How can we enhance our approach to compliance management? The integration of user-friendly interfaces further empowers healthcare staff to navigate complex regulations, making their work more manageable.
As the healthcare industry moves toward 2025, the emphasis on real-time monitoring and continuous training for staff cannot be overstated. By fostering a culture of compliance and vigilance, healthcare providers can significantly reduce the risk of data breaches and enhance patient trust. The collective efforts to implement these strategies not only protect patient information but also reinforce the integrity of healthcare delivery.
Ultimately, the commitment to comprehensive data security is not merely a regulatory obligation; it is a foundational aspect of compassionate and effective patient care. By embracing these essential components of a secure healthcare environment, organizations can navigate the complexities of modern healthcare while ensuring that the well-being of patients remains at the forefront. Together, let us prioritize these strategies and create a safer, more nurturing environment for all.




